Intel Sgx
- Référence externe : https://en.wikipedia.org/wiki/Software_Guard_Extensions
Intel’s hardware implementation of the enclave concept.
private regions of memory, called enclaves, whose contents are protected and unable to be either read or saved by any process outside the enclave itself
Should be fips 140-2 Level 3, (not 4) since it is indicated not to handle side-channel attacks.
flexible launch control
- Référence externe : https://software.intel.com/content/www/us/en/develop/blogs/an-update-on-3rd-party-attestation.html
What is Flexible Launch Control?
The Intel SGX DCAP primitives require a new feature called Flexible Launch Control, which allows the platform owner, versus Intel, to control which enclaves are launched. This includes which enclaves are granted access to the Platform Provisioning Identifier (PPID) used with the Certificate Retrieval Service. The enclave requesting access to the PPID can be signed by the attestation service provider. One of the purposes of the Launch Enclave is to prevent abuse of the PPID in privacy sensitive environments.
Building an attestation service requires integration with the operating system, and we are working with the Linux Kernel community to get this up-streamed as soon as possible. Note that you are not required to build your own Quoting Enclave.
— https://software.intel.com/content/www/us/en/develop/blogs/an-update-on-3rd-party-attestation.html
Ma compréhension
SGX est un ensemble de fonctionnalités de la suite des processeurs intel post 2018 permettant un chiffrement/déchiffrement à la volée de la DRAM avec une clé cryptographique embarquée dans le processeur.
Elle permet la réduction de la surface d’attaque à l’interface entre le processeur et la partie logicielle et entre le code de la partie chiffrée et le reste de l’application. [1]
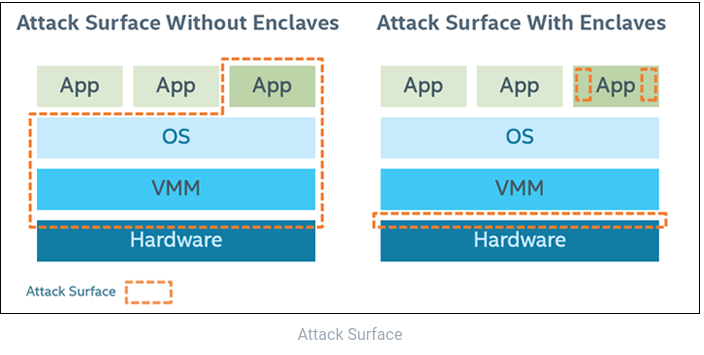
Il y a très peu de limitations à ce qui peut tourner de façon chiffrée, mais, dû à la corrélation entre nombre de bugs et taille de code et au sur coût de chiffrer à la volée, il est conseillé de réduire la partie chiffrée au minimum nécessaire à garantir la confidentialité du code. [2]
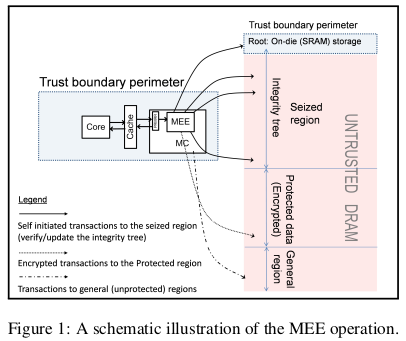
Il est important de comprendre que, dans le modèle de confiance de SGX, le circuit imprimé contenant le processeur est la seule entité de confiance, incluant la SRAM associée. La DRAM est considérée non de confiance. [3]
Bien que SGX tente de rendre l’écriture de programmes simples, il est nécessaire de comprendre les vocabulaire de SGX pour développer des application compatibles :
- ECALL, OCALL,
- measurement,
- attestation,
- …
Pour protéger la mémoire, voir how does sgx protects my data?
Notes pointant ici
- A Memory Encryption Engine Suitable for General Purpose Processors
- architectural enclaves
- asylo
- attacks on sgx
- attestation
- can I run sgx inside a virtual machine?
- Can I Use Intel’s SGX for Secure Computation in the Cloud Yet?
- common sgx installation issues
- Details of Intel® Software Guard Extensions
- download and install intel sgx driver and resources
- ECALL
- enclave de calcul sécurisée
- enclave page cache
- faire une sauvegarde de secret, c’est une faille de sécurité
- find out whether your hardware can play with sgx
- graphene
- How to Enable and Disable Intel SGX from the OVHcloud Manager – Articles
- how to know if my intel® processor supports intel® software guard extension
- how to play with sgx in azure?
- Improving Performance and Security of Intel SGX
- install the linux sgx driver
- intel memory encryption engine
- intel sgx encryption
- Intel SGX Explained
- Intel® SGX Technology and the Impact of Processor Side-Channel Attacks
- Intel® SGX Trusted Computing Base (TCB) Recovery
- Is sgx protected memory limit really 128MB?
- Load Value Injection
- Managing Intel SGX on an Infrastructure server | OVH Guides
- measurement
- noyau 5.11 de Linux
- OCALL
- PLATYPUS: With Great Power comes Great Leakage
- rust-sgx
- scontain
- setup sgx on cloud
- sgx dcap out-of-tree driver
- sgx documentation
- sgx drivers
- sgx out-of-tree driver
- sgx platform software
- sgx SDK
- SGX secure enclave in practice security and crypto review
- sgx-detect
- SGX: comment protéger vos données sensibles | Talium
- Solved: SGX models that support DCAP - Intel Community
- trusted computing base
- Using SGX in Virtual Machines - Intel Community
- when not to use sgx