A Memory Encryption Engine Suitable for General Purpose Processors
Fleeting- External reference: @cryptoeprint:2016:204
The whitepaper at the origin of the mee.
About the security of SGX
(sgx) run software in a trustworthy manner and to handle secrets.
adversary has full control of the system, and the software running on it at any privilege level, and can read or modify the contents of the DRAM
assumption that the security perimeter includes only the internals of the CPU package, and in particular, leaves the DRAM untrusted.
only components that SGX trusts are the CPU internals
The chip (on-die) is trusted, so the SRAM is trusted, but not the DRAM.
(sgx needs) full DRAM protection for confidentiality, integrity, and anti-replay.
SGX requires memory protection […] requires that the confidentiality of CPU-DRAM traffic (within the relevant regions) is protected.
in order to trust an enclave’s cryptographic identity, its intended execution flow, and the attestation protocol, the DRAM (at least part of) must be tamper resistant
Or the attacker could change the attested memory just after the security checks are done. This is why
replay prevention is critical
The role of the MEE
supported by an autonomous hardware unit called the Memory Encryption Engine (MEE), whose role is to protect the confidentiality, integrity, and freshness of the CPU-DRAM traffic over some memory range
(this document) explains how this hardware (MEE) component of SGX works
The design of the MEE
design is based on the following pillars: an integrity tree, the cryptographic primitives that realize the encryption, the Message Authentication Code (MAC), and the anti-replay mechanism.
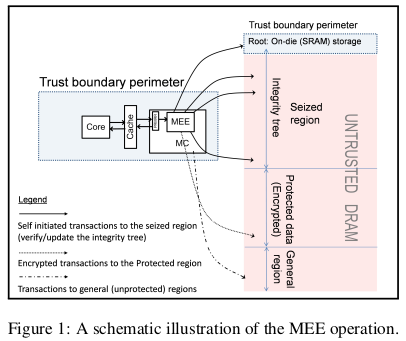
internal (on-die) storage is limited and expensive. This requires that the system seizes a dedicated dram region where the tree can be stored and maintained.
The SRAM is trusted, but limited, the DRAM is not trusted but available. Then, the idea is to have an integrity tree, whose root is in the trusted SRAM but whose content is in the entrusted DRAM.
some on-die SRAM array that serves as the root of the tree.
How it works
MEE operates as an extension of the MC (NDR: memory controller), taking over the cache-DRAM traffic that points to what is called the “Protected” data region. An additional portion of the memory, called the “seized” region, accommodates the MEE’s integrity tree.
Read/write requests to the protected region are routed by the MC to the MEE that encrypts (decrypts) the data before sending (fetching) it to (from) the DRAM
range of physical addresses that is fixed to some size at boot time (the default size is 128MB), in a trustworthy way.
see Is sgx protected memory limit really 128MB?
I understand that the Protected data region is the so called processor reserved memory.
“drop-and-lock” policy
Understood as: The MEE compares the computed tag MAC with the integrity tree data and locks the computer if the data mismatch at any time.
About the integrity tree.
Trusting only the internally stored root of the tree, that cannot be modified by an adversary, is sufficient. […] successful forgery needs to pass the MAC tag check with an unmodified nonce for at least one location on the tree.
using MAC tags is typically more efficient than using hashes
The MEE integrity tree uses a stateful MAC with nonces
A simplified tree model […] the MEE data structure.
requires the encryption scheme to use a non repeating location-time tweak. The MEE uses a compound nonce where the spatial coordinate of a unit is its address, and its temporal coordinate is a dedicated per-unit counter
About the cryptography
The MEE encryption scheme is a “tweaked” AES Counter Mode
Against replay attack
The preemptive check is crucial […] This allows a successful replay (NDR: attack)
Non-repeating compound nonces. The tree updating must assure that nonces do not repeat. […] The MEE uses a […] “compound nonce” construction.[…] a) a unique “spatial coordinate” (address) of the data unit; b) a per-unit counter which is a “temporal coordinate”.
The MEE uses a compound nonce where the spatial coordinate of a unit is its address, and its temporal coordinate is a dedicated per-unit counter.
equal plaintext blocks that are encrypted to different addresses and/or at different points in time, should not translate to equal ciphertext blocks.
Two dimensional nonce (spatial and temporal) to make sure the encrypted data is always different.
Performance
the MEE imposes performance degradation that varies from 2.2% to 14%, with an average of 5.5%
Side notes
cryptographic measurement (SHA-256 digest)
Is it the same measurement as the one in the enclave measurement?