Sgx 101
Fleeting- External reference: @34b4bd29126a7099a40d3e7edbb0c92e60b152c1
- External reference: https://sgx101.gitbook.io/sgx101/sgx-bootstrap/enclave/interaction-between-pse-and-application-enclaves
- See also sgx documentation
- Parts
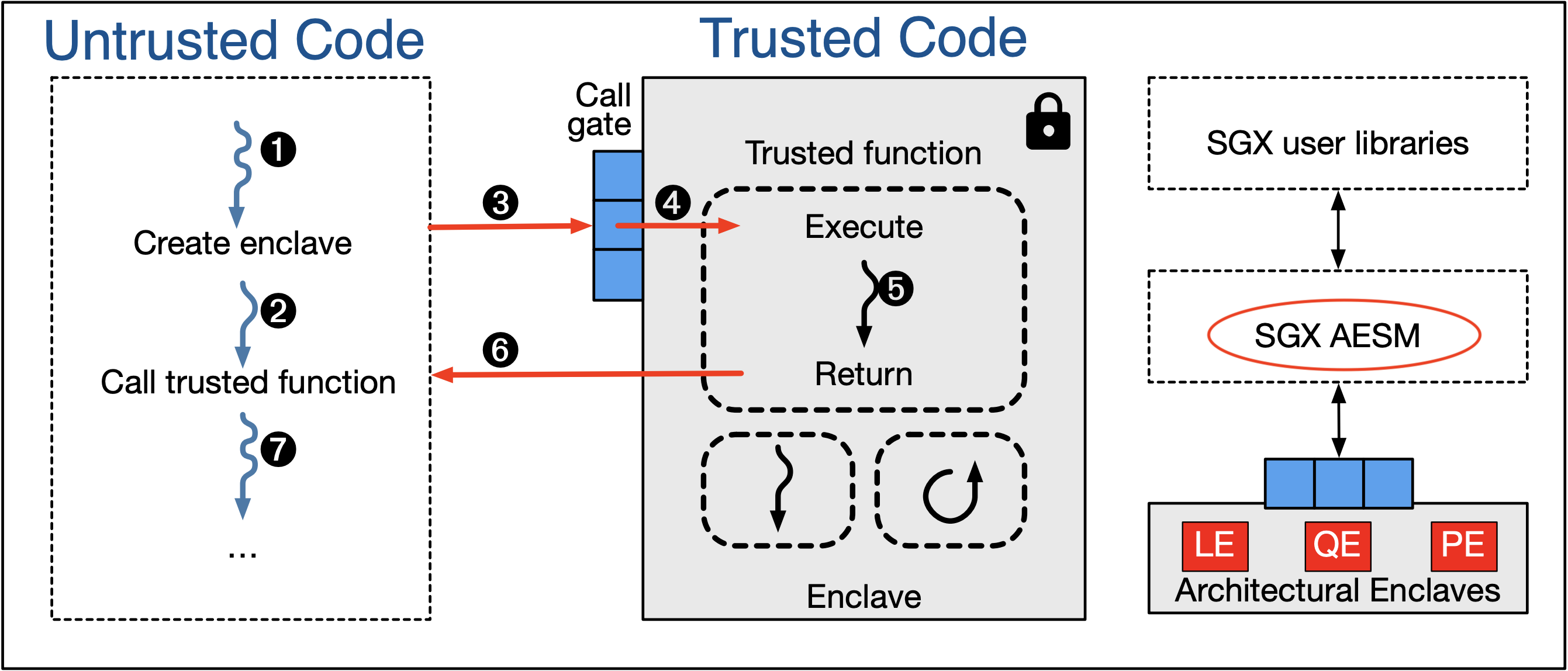
What are architectural enclaves?
In order to allow a secured SGX environment to execute, several Architectural Enclaves (AE) are involved.
Launch Enclave (LE)
Launch Enclave is responsible for assigning EINITTOKEN to other enclaves wishing to launch on the platform. It verifies whether the requesting enclave is valid or not by examining the enclave’s signature and identity, and generates the EINITTOKEN from Launch Key, which is only available to Launch Enclave.
Provisioning Enclave (PvE)
The Provisioning Enclave is responsible for retrieving the Attestation Key from Intel Provisioning Service using the certificate provided by Provisioning Certificate Enclave.
Provisioning Certificate Enclave (PcE)
Provisioning Certificate Enclave is responsible for signing the processor certificate, which is requested by the provisioning enclave. It signs the certificate using the Provisioning Key, which is only available to Provisioning Certificate Enclave.
Quoting Enclave (QE)
Quoting Enclave is responsible for providing trust in the enclave identity and its execution environment during remote attestation process. It uses the Attestation Key offered by Provisioning Enclave and turns a REPORT (locally verifiable) into a QUOTE (remotely verifiable).
Platform Service Enclaves (PSE)
Platform Service Enclaves are responsible for offering other enclaves various trusted services, such as monotonic counters and trusted time, using Management Engine (ME).
In order to allow a secured SGX environment to execute, several Architectural Enclaves (AE) are involved
enclave’s code and data is stored in Processor Reserved Memory (PRM),
two exchanging enclaves have to prove to each other that they can be trusted
How do Application Enclaves communicate with Architectural Enclaves to utilize SGX services?Simply put, it is through Intel SGX AESM, the Application Enclave Service Manager
AESM is the system services management agent for SGX enabled applications.
Those services include various components of the SGX system, such as launch approval, remote attestation quote signing, etc.
AESM is a part of SGX Platform Software
AESM runs as a daemon process aesmd when the system starts
All the messages transmitted between Architectural and Application Enclaves will go through AESM via this socket, and processed accordingly.
any communication between Architectural and Applications Enclaves requires AESM support, including enclave launch approval