Multi-Factor Authentication
Fleeting- External reference: https://en.wikipedia.org/wiki/Multi-factor_authentication
- External reference: https://en.wikipedia.org/wiki/Multi-factor_authentication#MFA_fatigue
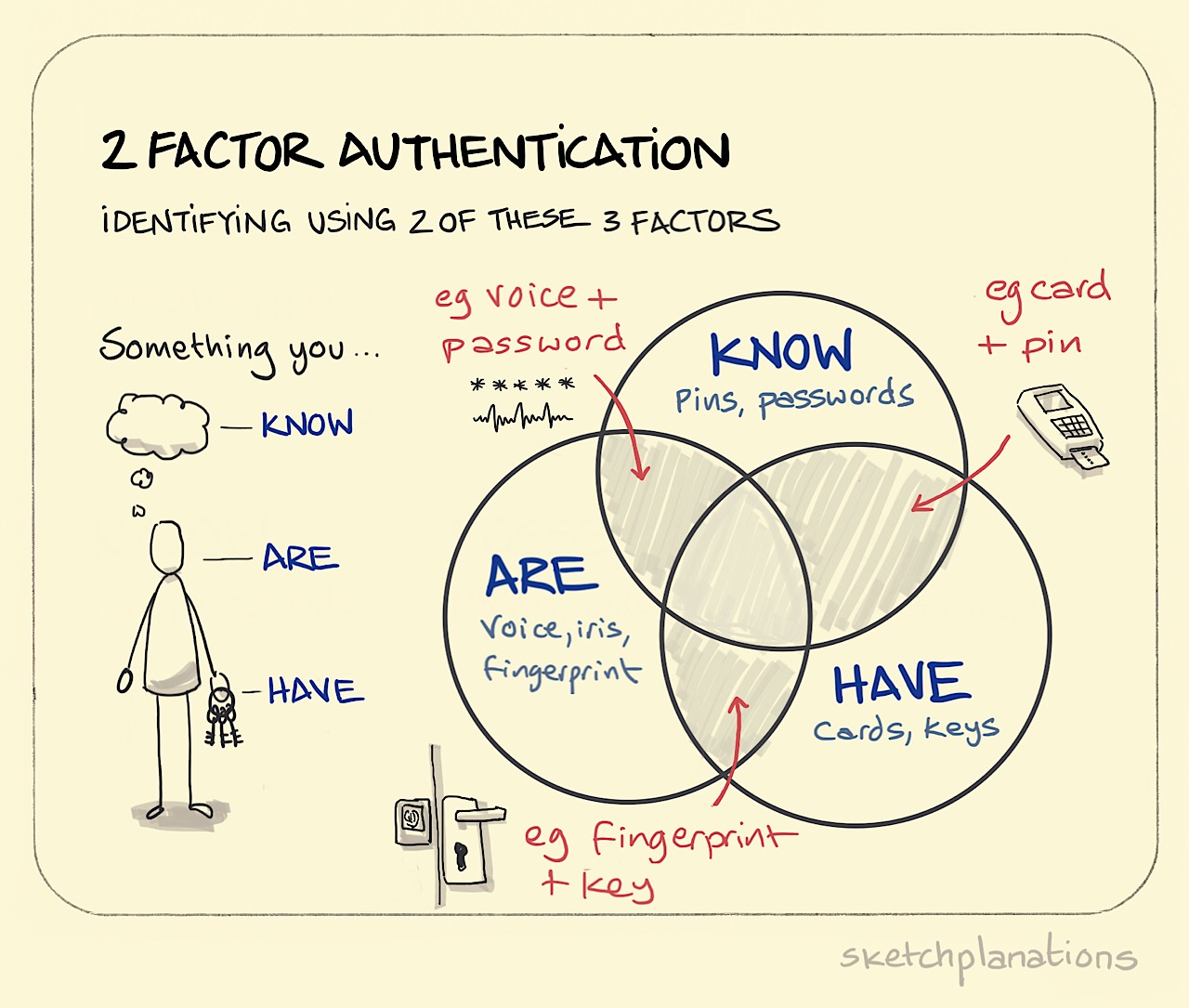
Using more than one factor to authenticate a user, not necessarily including password1.
factor
knowledge (something only the user knows),
possession (something only the user has),
and inherence (something only the user is).
location (somewhere the user is),
ambiguity
I have heard people raise a semantic debate where authenticating several times using the same nature of authentication may be called MFA. For instance, a colleague called 2FA password authenticating twice from two distinct Identity Providers (hence two methods about “something you know”).
Per also claimed that whatever the nature, as long as the authenticating services asks for N pieces of evidence, then it becomes NFA.
Per main argument was that the introduction of the wikipedia page says so.
presenting two or more pieces of evidence (or factors)
[…]
may require more than one factor—multi-factor authentication, or two-factor authentication in cases where exactly two pieces of evidence are to be supplied
Indeed, this articles appears to say that a factor is a piece of evidence, not a TYPE of piece of evidence. It suggests that the TYPEs may only be good practices.
Puzzled by the assertion of my colleague, I dug a little deeper. I even followed the wikipedia citations :-).
I realized that a lot of definitions lack clarity, defining a factor as a piece of evidence or simply not defining it at all3. But even more clarified that it is about the TYPE of the piece of evidence4 and not about the number of pieces. Some did even provide examples of what is NOT MFA5, like asking two passwords.
I did not find a “first definition” that would end the debate. It appear to be first used in a patent, so I probably never (pay to) read this definition.
Yet, I decided to believe that this is only bad phrasing and that there is a huge consensus to say that a factor is a TYPE of authentication. Even sites that provide poor definition still appear to convey this idea. And I did not find any not site claiming that such things as password and question phrase could be named 2FA. It appears to be difficult to spend some time looking for a definition at eventually believing this.
Actually, even the sources (I did not look at all of them though) of the wikipedia page are about TYPES of evidence.
For example, the source of the previous citation says:
I understand that this might undergo the naming things tragedy. Yet the consensus appear to be very strong and I guess people like my colleague did not read much nor think much about it. Even the name should tell, because if factors where just pieces of evidences, Multi Authentication would summarize it well.
In the end I encourage people to try to go beyond the wording and discuss what they are trying to achieve in term of security before entering an unwanted semantic debate. For instance, asking for a TOTP and a personal security device may well be a very good design in some cases, whatever we decide to call it 1FA or 2FA.
CTR outlines the following challenges:
Ambiguity with MFA terminology
fatigue
An increasingly common approach to defeating MFA is to bombard the user with many requests to accept a log-in, until the user eventually succumbs to the volume of requests and accepts one
— https://en.wikipedia.org/wiki/Multi-factor_authentication#MFA_fatigue
two-factor authentication
Notes linking here
- 2 factor authentication
- are IT guys the one that undergo phishing?
- authentication vs identification vs authorization
- Getting 2FA Right in 2019
- misconcetions
Permalink
-
↩︎Note that a password is not required to qualify for MFA. An MFA solution can be entirely passwordless.
— https://www.onespan.com/topics/multi-factor-authentication
-
three main categories:
- Something you know (knowledge factor)
- This is typically a password, PIN, or passphrase, or a set of security questions and their corresponding answers known only to the individual. To use a knowledge factor for MFA, the end user must correctly enter information matching details that were previously stored in the online application.
- Something you have (possession factor)
- Before smartphones, users carried tokens or smartcards that generated a one-time password or passcode (OTP) that could be entered into the online application. Today, most users install an authenticator app on their smartphone to generate OTP security keys.
- Something you are (inherence factor)
- Biometric data about an individual ranges from fingerprints, retina scans,
facial recognition, and voice recognition to behaviors (such as how hard or
fast the person types or swipes on a screen).
— https://www.onespan.com/topics/multi-factor-authentication
three most common kinds of factors are:
- Something you know - Like a password, or a memorized PIN.
- Something you have - Like a smartphone, or a secure USB key.
- Something you are - Like a fingerprint, or facial recognition.
four different types of evidence (or factors) that can be used, listed in the table below:
Factor Examples Something You Know Passwords, PINs and security questions. Something You Have Hardware or software tokens, certificates, email, SMS and phone calls. Something You Are Fingerprints, facial recognition, iris scans and handprint scans. Location Source IP ranges and geolocation — https://cheatsheetseries.owasp.org/cheatsheets/Multifactor_Authentication_Cheat_Sheet.html
↩︎- knowledge (something only the user knows),
- possession (something only the user has),
- and inherence (something only the user is).
[…] fourth factor is coming into play involving the physical location of the user
-
Multi-factor Authentication (MFA) is an authentication method that requires the user to provide two or more verification factors to gain access to a resource such as an application
requires users to provide more than one credential to prove their digital identity
MFA works by requiring additional verification information (known as factors)
↩︎MFA requires multiple pieces of evidence to verify identity.
— https://www.cisco.com/c/en/us/products/security/what-is-multi-factor-authentication.html
-
A factor in authentication is a way of confirming your identity when you try to sign in
account login process that requires multiple methods of authentication from independent categories of credentials
— https://www.techtarget.com/searchsecurity/definition/multifactor-authentication-MFA
Multi-factor authentication (MFA) uses multiple technologies to authenticate a user’s identity
— https://www.onespan.com/topics/multi-factor-authentication
Multifactor authentication combines two or more independent credentials – what the user knows, such as a password; what the user has, such as a security token; and what the user is, by using biometric verification methods
— https://www.techtarget.com/searchsecurity/definition/multifactor-authentication-MFA
#+END_QUOTE
Multi-Factor authentication (MFA), or Two-Factor Authentication (2FA) is when a user is required to present more than one type of evidence in order to authenticate on a system
— https://cheatsheetseries.owasp.org/cheatsheets/Multifactor_Authentication_Cheat_Sheet.html
Through several verification methods, such as phone, SMS, and mobile app verification, it offers robust authentication. MFA’s security comes from its layered approach.
Multi-factor authentication (MFA) takes two or more authentication methods from different categories to confirm a user’s identity
Multi-factor authentication (MFA) is a user verification method that requires more than one type of user validation
authentication system that requires more than one distinct authentication factor for successful authentication
[…]
three authentication factors are something you know, something you have, and something you are.
Authentication using two or more factors to achieve authentication. Factors include: (i) something you know (e.g., password/personal identification number [PIN]); (ii) something you have (e.g., cryptographic identification device, token); or (iii) something you are (e.g., biometric)
Proper multi-factor authentication uses factors from at least two different categories. Using two from the same category does not fulfill the objective of MFA
— https://www.cisco.com/c/en/us/products/security/what-is-multi-factor-authentication.html
↩︎2FA requires the user to have two out of three types of credentials before being able to access an account. The three types are:
- Something you know, such as a personal identification number (PIN), password or a pattern
- Something you have, such as an ATM card, phone, or fob
- Something you are, such as a biometric like a fingerprint or voice print
— https://www.cnet.com/news/privacy/two-factor-authentication-what-you-need-to-know-faq/
-
single factor (such as needing both a password and a PIN) does not constitute MFA, although it may provide some security benefits over a simple password
— https://cheatsheetseries.owasp.org/cheatsheets/Multifactor_Authentication_Cheat_Sheet.html
Despite wide use of the password/security question combination, both factors are from the knowledge category–and don’t qualify as MFA. A password and a temporary passcode qualify because the passcode is a possession factor, verifying ownership of a specific email account or mobile device
— https://www.cisco.com/c/en/us/products/security/what-is-multi-factor-authentication.html
↩︎using a PIN with a password (both from the “something you know” category) would not be considered multi-factor authentication, while using a PIN with facial recognition (from the “something you are” category) would be
— https://www.onespan.com/topics/multi-factor-authentication