Ledger Vault
Fleeting- External reference: https://konubinix.eu/ipfs/bafybeidqldry65utdtitubf7xelfg5xveukjmbma25fefv5k223yzb5o54
- External reference: https://vaultplatform.ledger.com/
- External reference: https://vaultplatform.ledger.com/why-vault
Solution de gestion des clefs de blockchain de ledger (company)
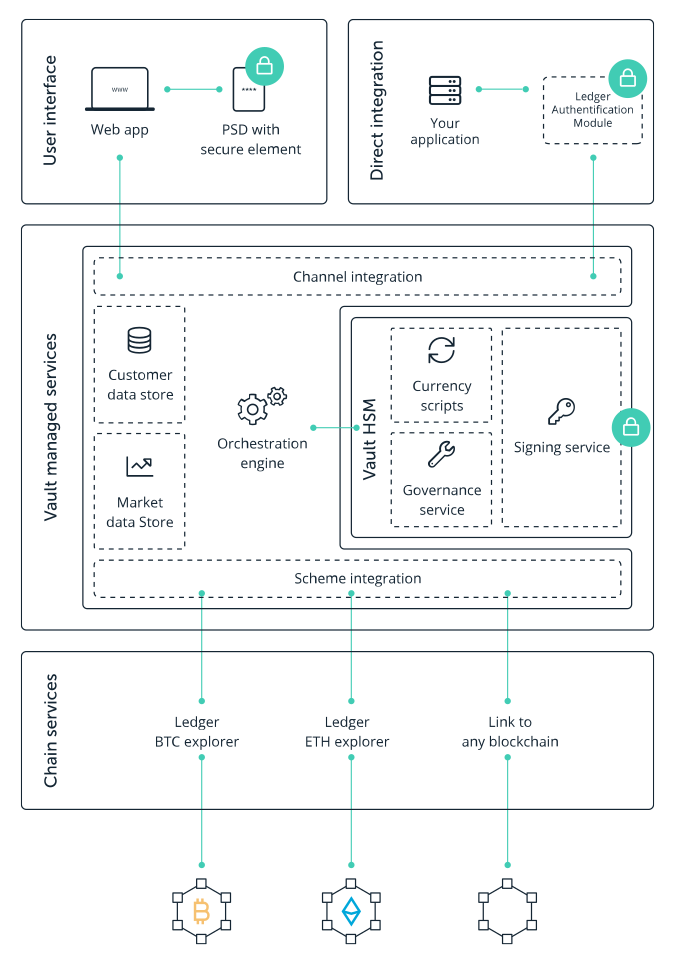
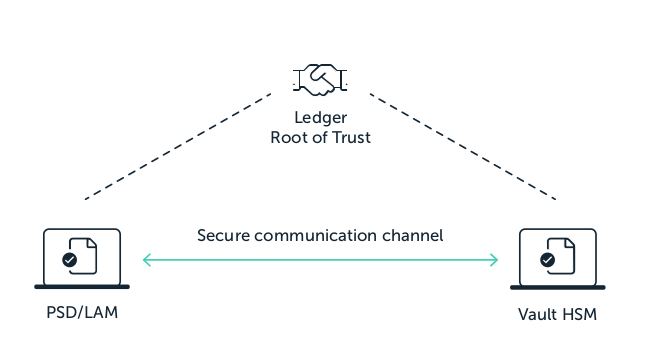
Every user confirms their actions with a personal security device running the Vault application. A secure channel is created between the device and the HSM in order to ensure strong authentication.
if a transaction amount below a specific threshold is requested, the HSM may only require a quorum of approval from the back office team, but if the transaction is above a specific threshold, the HSM may require additional approval from the compliance team or from a group of users in a different geographic location
Each user requires a Personal Security Device (PSD) to interact with the Vault platform
Communications are secured end-to-end from the user devices to the HSM
governance framework entirely protected within Secure Hardware
Key concepts
Personal security devices (PSD) and hardware security modules (HSM) are two fundamental components underpinningthe Vault platform. A glance into each element brings further insights into the Vault service architecture.
Personal security devices for Wysiwys (What-You-See-Is-What-You-Sign)
details on a Ledger Personal Security device before the information gets is one of the critical components of the security design of the platform.
Maintaining this guarantee was one of our key concerns while building the Ledger Vault APIs, which led us to design an architecture based on a client- infrastructure rather than Ledger’s, the LAM is able to securely isolate the secrets that will be used to authenticate and communicate with your Vault.
on to the Master Seed fragments for disaster recovery purposes. It is important to note that this ensures daily users never have direct interaction with any sensitive
Wrapping Key
Custodians generate the wrapping Operators oversee the process of creating, reviewing key which is used to encrypt your organization’s HSM partition
The multi-authorization feature
distributes the signing Approval groups allow for the creation of complex responsibility among multiple Operators within the multi-authorization schemes based on organizational institution. These operators can then be geographically distributed across the world if needed.
The whitelist enables to block outbound transactions
24-words recovery sheets created by the Shared Owners.